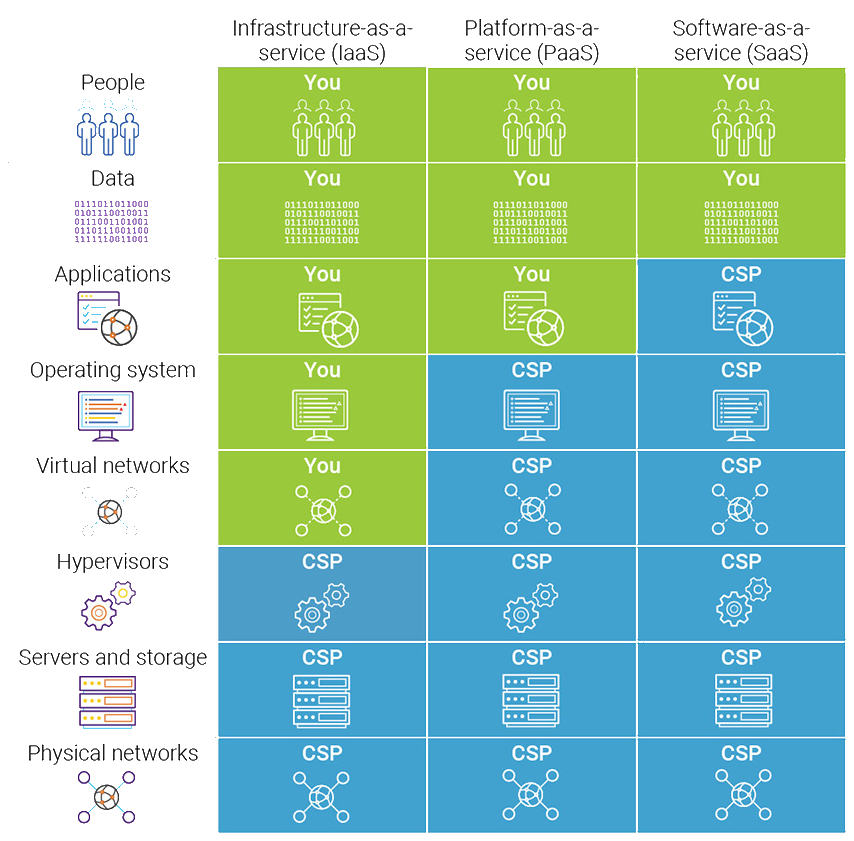
The shared responsibility model defines the limits of responsibility for cloud security in the provider/customer relationship. The responsibilities model varies for the different types of services, IaaS, PaaS and SaaS.
IaaS – Infrastructure as a Service, for example: servers, network, and cloud storage
PaaS – Platform as a Service, for example: SQL service without a server
SaaS – Software as a Service, for example: Salesforce service
You should know the differences between the solutions, the implications for security, and what you, the customer, are responsible for.
With so many providers, platforms, tools, and services in the IaaS, PaaS, and SaaS categories, organizations need to understand the distribution of responsibilities for cloud security that can be misleading and not always clear. Organizations tend to think that in fact moving to the cloud they become secure, without realizing that in most cases, the responsibility for security and implementation of appropriate solutions is theirs and not the cloud provider’s. Organizations need to ask themselves whose information they will store in the cloud irrelevant to the service model, a question to which the answer is usually clear, but in fact in the body of the answer that will arrive lies the answer as to who is responsible for securing that information.
With traditional on-prem local data centers, the company’s IT team is fully responsible for all data as well as the physical infrastructure. This fact makes the whole security process relatively “simple”. Of course it is not “simple” and extensive knowledge must be kept up to date in order to provide an appropriate solution.
When they move to the cloud, IT teams have to deal with cloud vendor infrastructure and services, a fact that tends to complicate the organization’s overall security strategy, and also that most cloud infrastructures are directly connected to the Internet, a fact that further challenges security requirements and is sometimes “easier” to organize. Understand and deal with it in a “simpler” way in On-Prem solutions.
In a cloud solution, the vendor assumes some of the responsibility associated with environmental security, but not necessarily the data held within it. This can be extremely helpful for many IT teams, but if administrators and developers do not secure operating systems and applications, the organization may be exposed to many security threats, no matter how secure the cloud infrastructure may be and may even meet security standards that cover only the infrastructure, but not the The applicative environment and / or information of the organization.
The key to a successful cloud security strategy is understanding the shared responsibility model for both parties.
IaaS, PaaS and SaaS security models
Before diving into the details of a shared responsibility model in the cloud, IT teams must understand the security differences in the different types of service models. These services dictate what the supplier is responsible for or not responsible for.
With the IaaS model, the vendor is responsible for securing the physical data centers and hardware that runs the infrastructure, including “host” servers, storage, and the “core” network. The customer must secure the data, operating systems, virtual network, software layer and applications that he runs in the cloud. In this model, the client is responsible for many aspects of the solution, but he has the option to use the cloud provider, depending on the provider and the options he makes available to the client of course, to also manage the logical security of the client’s virtual servers.
PaaS is an “intermediate” step when it comes to the shared responsibility model for cloud security, and places more responsibility in the hands of the cloud provider. In this scenario, the customer’s IT team still manages the applications and data, but the vendor secures the basic infrastructure operation and also adds to its responsibility the operating systems and platform that the customer uses, for example databases.
In the SaaS model, the customer has no control at all over the software layer and he actually shifts the entire responsibility to the supplier. A SaaS vendor is responsible for all levels of security in the solution it provides, from the infrastructure level to the software level. IT teams only need to manage permissions, depending on the tools provided by the vendor.
Keep in mind that in most cases, SaaS vendors rely on the infrastructure of other IaaS vendors, and in fact create an additional layer of responsibility for the security of the solution that is shared between multiple vendors. Keep in mind that a “software as a service” provider, ie SaaS, at the end of the day provides a software service for which it is solely responsible from end to end, In case he hosts the software on another provider’s IaaS infrastructure service, the IaaS provider has a clear role in the responsibility for infrastructure security and may have appropriate standards, but is not a partner in software security, ie the product that the customer needs from the SaaS provider. Compliance with the infrastructure provider’s standards in the IaaS service does not imply the standard right also to the SaaS provider who is solely responsible for the software, in which case he must present an appropriate standard exclusively for the product he provides, regardless of the infrastructure on which the product is hosted. The product / software and installation is not relevant to this layer.
Enforcement of the model
Cyber attacks and security threats in the cloud are on the rise, some of us are exposed to them in the press and some of us are even involved in situations on a regular basis. Most notable security breaches, which tend to be very costly for the affected organization, are caused as a result of misleading on the customer side and / or at the software level and not provided by the cloud.
Working with a cloud provider may be less clear for some organizations when there is no coordination of expectations and an understanding of the division of responsibilities. From the first day of the contract, a clear division of responsibilities between the cloud provider and the customer must be determined and the teams outlined a clear outline that shows where the cloud provider’s security ends, where the customer’s responsibility begins and sometimes where the responsibility arises for joint discussion.
When it comes to a shared responsibility model in the cloud, there is no room for assumption and nothing should remain “in the air”. To ensure that there is a mutual understanding between the cloud provider and the customer, expectations must be accurately coordinated using a clear SLA document for both parties.
If the cloud provider also has an integration department, the issue may be very easy for the customer as the cloud provider’s integration department is well skilled with all the tools and options and will be able to provide the customer with the peace of mind, as well as advise and share professional knowledge and sometimes remove different responsibilities in the journey to the cloud.
Tomer Schwaitzer is the founder of the y-tech Group and Israel’s representative on the World Standards Committee for Cloud Computing in the ISO / IEC JTC1 organization